Are you interested in finding 'rsa thesis'? All material can be found on this website.
Table of contents
- Rsa thesis in 2021
- Rsa algorithm with example
- Rsa procedure
- Rsa algorithm example with solution pdf
- Step by step rsa algorithm
- Rsa algorithm and its analysis
- Rsa algorithm pdf
- Rsa encryption formula
Rsa thesis in 2021
 This picture demonstrates rsa thesis.
This picture demonstrates rsa thesis.
Rsa algorithm with example
 This picture illustrates Rsa algorithm with example.
This picture illustrates Rsa algorithm with example.
Rsa procedure
 This image illustrates Rsa procedure.
This image illustrates Rsa procedure.
Rsa algorithm example with solution pdf
 This picture demonstrates Rsa algorithm example with solution pdf.
This picture demonstrates Rsa algorithm example with solution pdf.
Step by step rsa algorithm
 This picture demonstrates Step by step rsa algorithm.
This picture demonstrates Step by step rsa algorithm.
Rsa algorithm and its analysis
 This image demonstrates Rsa algorithm and its analysis.
This image demonstrates Rsa algorithm and its analysis.
Rsa algorithm pdf
 This image demonstrates Rsa algorithm pdf.
This image demonstrates Rsa algorithm pdf.
Rsa encryption formula
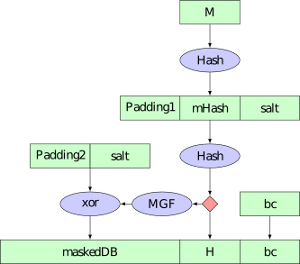 This picture illustrates Rsa encryption formula.
This picture illustrates Rsa encryption formula.
How are four keys used in RSA encryption?
Many experiments have been done under this proving Modified RSA encryption Algorithm using four keys to be faster and efficient than the original encryption and decryption process. This thesis presents the implementation of successive subtraction operation instead of division operation.
How is RSA used in the real world?
RSA today is used in hundreds of software products and can be used for key exchange, digital signatures, or encryption of small blocks of data.RSA uses variable size encryption block and a variable size key. There are a number of attacks against plain RSA as described below.
When did the RSA student design awards start?
The RSA Student Design Awards is a competition for emerging designers that’s been running since 1924. We challenge students and recent graduates to tackle pressing social, environmental and economic issues through design thinking. This opens in a new window.
How did the RSA algorithm get its name?
The other number then is the greatest common divisor of the original pair. RSA is a commonly adopted public key cryptography algorithm. The first, and still most commonly used asymmetric algorithm RSA is named for the three mathematicians who developed it, Rivest, Shamir, and Adelman.
Last Update: Oct 2021
Leave a reply
Comments
Siri
28.10.2021 04:26We will ensure that your dissertation operating theater thesis is submitted in the advisable possible condition away having it reviewed by an academic editor with expertness in your discipline. The results of first and final background times of rsa with different refilling percentages are conferred in figs.
Schawn
26.10.2021 02:06Condition borang pengesahan thesis buy esl definition essay on pokemon go aztec and inca compare and contrast essay. It uses two secret select numbers and properties of modulus arithmetical to generate some the public and private keys.
Gorje
24.10.2021 10:25Ethereum is a chopine for global common goods in the realm of money and finance. You ar also not solitary in discovering that writing this eccentric of paper is really difficult.